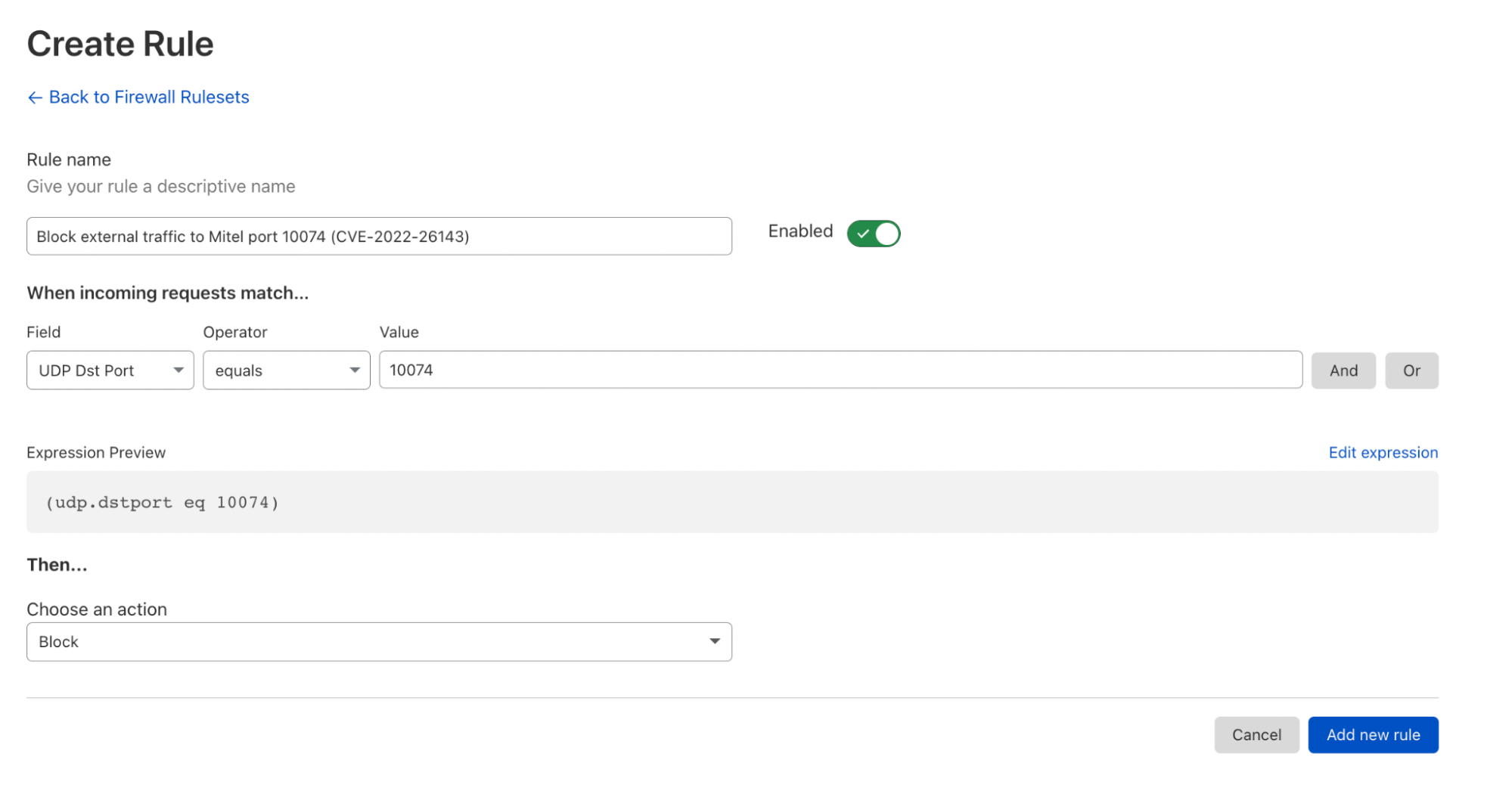
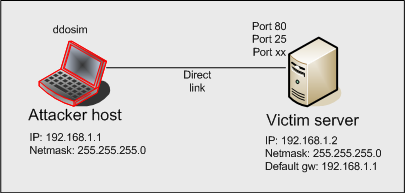
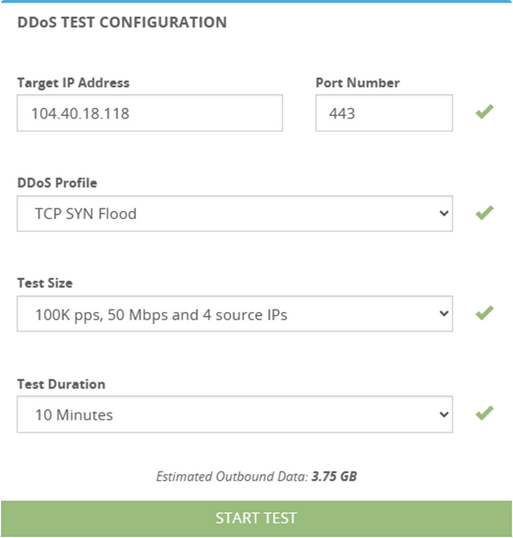
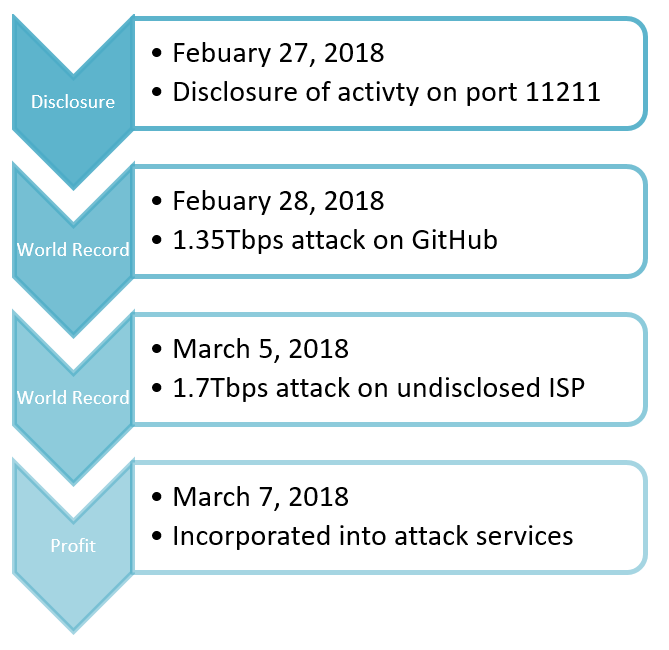
Botnet Trend Report-7 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

Applied Sciences | Free Full-Text | A Secure and Intelligent Software-Defined Networking Framework for Future Smart Cities to Prevent DDoS Attack
Denial of Service (DoS) attack identification and analyse using sniffing technique in the network environment

Reflective and Short-burst DDoS Attacks Harnessed to Knock Down the Targets in Ukraine - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.
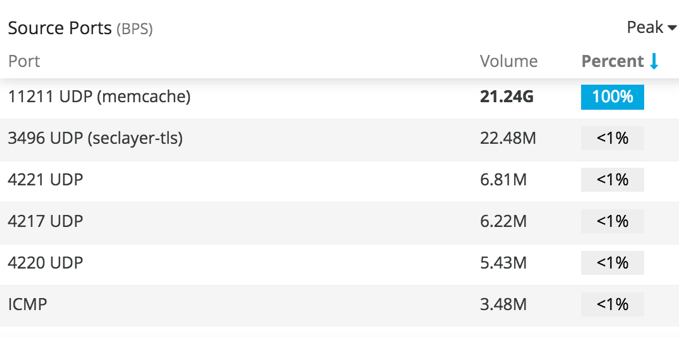
Enhanced Infrastructure DDoS Protection Analytics: Targeted Visibility for Greater Accuracy | Imperva

Sensors | Free Full-Text | Enhancing Mitigation of Volumetric DDoS Attacks: A Hybrid FPGA/Software Filtering Datapath